How to register your account with Evidian Enterprise SSO As a Service
Procedure
- After having the Enterprise SSO client installed on your workstation, the registration window appears:
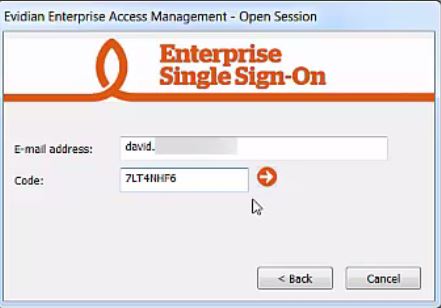
After you have typed in your e-mail, an OTP is sent by e-mail.
Enter the OTP you have received and click on Submit.
- Fill in your personnal information (optional). Type in your mobile number if you wish to enable authentication with OTP sent by SMS.
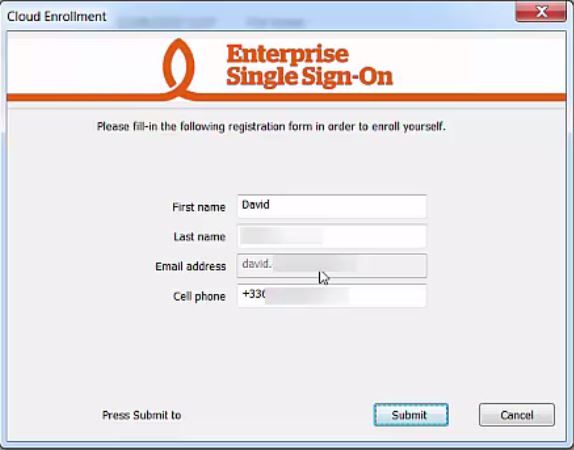
Click on Submit
- You now have access to your Enterprise SSO environment
Identity as-a-service
Evidian takes care of everything related to your Identity and Access Management with IDaaS
Learn more >
Identity Governance and Administration
Manage access and authorization of all your users in your company
Learn more >
Web Access Manager
Gateway for web apps with SSO, multi-factor authentication, identity federation
Learn more >
Authentication Manager
Authentication Manager
Enterprise multi-factor & passwordless authentication on Windows PCs
Learn more >
Enterprise Single Sign-On (SSO)
Secure access to legacy and web apps on PCs & mobiles with SSO